intro to jax: a permissionlessly incentivized storage layer for ethereum
what i got up to the other week
I was very happy to try and tackle the problem of decentralized storage this year at EthDenver. I started my journey as a software engineer trying to bring a decentralized storage product to market through my with banyan. This problem is very near and dear to my heart, both due to how interesting it is, and how vital it is for building a resilient, censorship-resistant, and private internet. One aspect of the current solution space that I wanted to address in my project was data availability. Current solutions like Filecoin and Arweave aren’t great at incentivizing peers to provide files to people who actually want them, so much as implementing mining incentives over their replication. This is valuable, but:
- leaves retrievability a second class citizen, whereas I wanted to make serving content the primary incentive
- requires storage to be tightly couple to a utility chain, making programming incentives restrictive It would be great if we had a way to reward peers for actually acting as service providers for peers on a decentralized network, and to be able to write reward mechanism directly on ethereum (or any EVM compatible chain).
My team and I ended up building and submitting jax: a permissionlessly incentivized storage layer for ethereum.
Links
Presentation
Trust-Based Availability as the Foundation
At its core, Jax evaluates peers based on their responses to real-time challenges that verify they’re actually storing and serving files. This creates several important distinctions from existing systems:
-
We use continuous challenge-response verification where peers must provide zk-proofs that they’re storing randomly targetted chunks of files. Only peers with the actual data can respond correctly.
-
Reputation emerges from demonstrated behavior rather than economic commitments. Your trust score reflects consistent performance, not staked tokens.
-
We make data availability a first-class concern. The system directly measures and rewards retrievability, ensuring data isn’t just allocated but accessible.
What’s particularly powerful is what Jax deliberately doesn’t do:
- No complex proofs of replication (unlike Filecoin)
- No elaborate hand wavy tokenomics for permanence (unlike Arweave)
- No heavy staking requirements that create high barriers to entry (at least in order to earn rewards)
Instead, Jax creates an economic model that rewards what users actually care about: can I get my data when I need it?
Technical Architecture: Blake3, Iroh, and EigenTrust
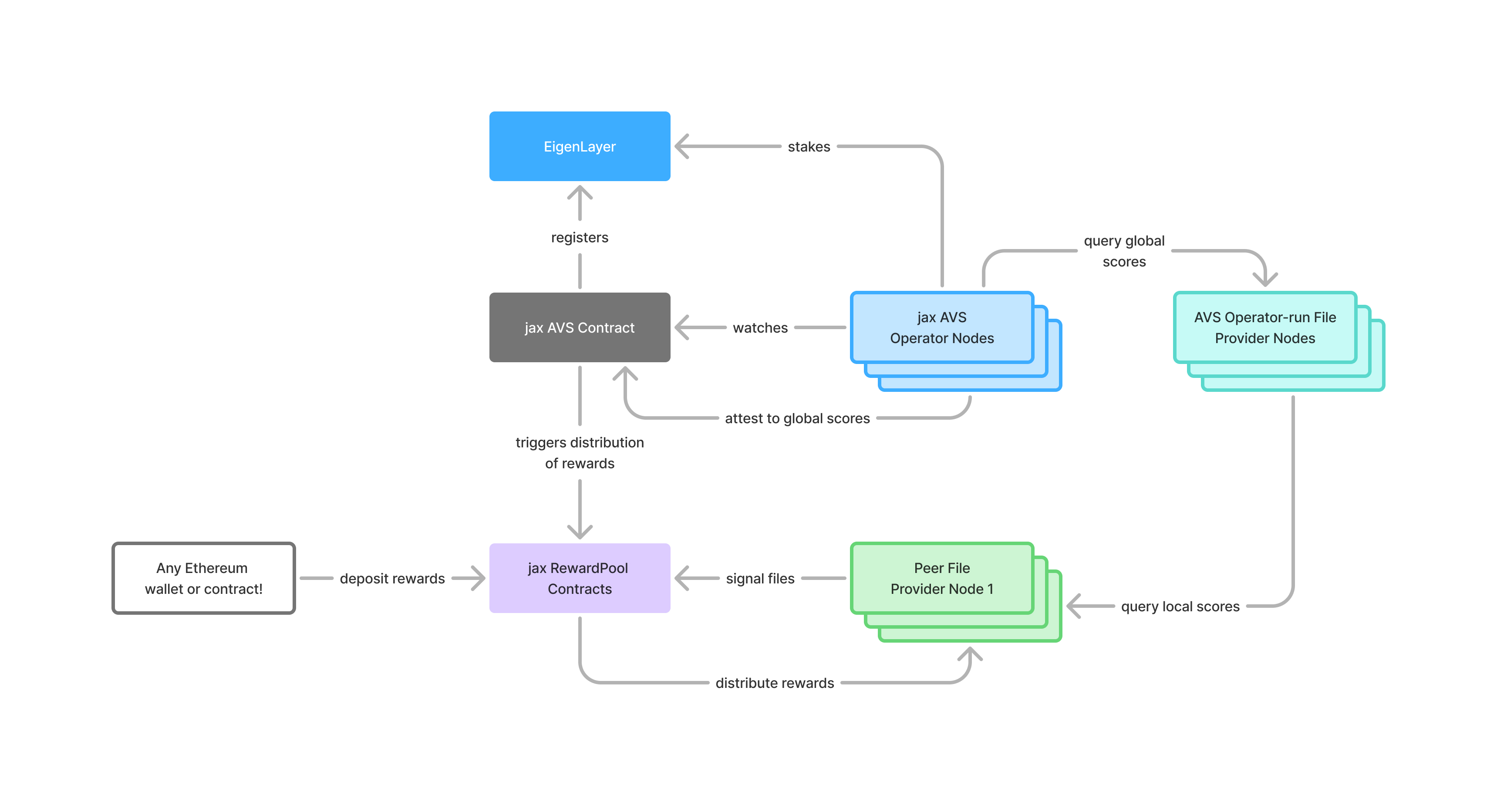
Our implementation leverages three key technical primitives:
Blake3’s Merkleized Structure: This cryptographic hash function processes files in 1KB chunks and forms a Merkle tree, enabling efficient verification of specific chunks without processing entire files. When a peer claims to store a file, others can challenge them to provide a proof for any random chunk. The challenged peer must have the actual data to produce the correct succinct proof, creating an elegant verification mechanism.
Iroh for P2P Networking: Our file provider nodes use Iroh to establish peer connections, distribute content, and exchange storage proofs. Iroh uses Ed25519 keys for node identity, which serve dual purposes: they authenticate Ethereum addresses for reward distribution and enable peer discovery. Unlike systems requiring complex sealing/unsealing, Iroh facilitates immediate file availability.
EigenTrust-Inspired Consensus: Perhaps the most innovative aspect is our distributed trust evaluation framework. The system algorithmically combines observations from multiple independent validators to form reliable consensus about peer behavior. Each operator issues cryptographic challenges based on Blake3 hashes and verifies responses, building local trust assessments that incorporate accuracy, latency, and consistency. Operators then come to consensus about the state of the network, and distribute rewards accordingly.
Our ETHDenver Implementation: Honest Assessment
For the hackathon, we built a functional system with three components:
- Smart contracts coordinating AVS operators and encoding reward distribution logic
- Eigenlayer AVS operator implementation calculating trust scores
- File provider nodes using Iroh for networking and storage proofs
However, we made several pragmatic shortcuts to meet the deadline. The most significant was implementing only local EigenTrust rather than the full gossip-based distributed algorithm. In a complete implementation, operators would exchange local observations through a peer-to-peer gossip protocol, with cryptographically signed messages propagating throughout the network.
Once sufficient observations are collected, the aggregation process would filter outliers, weight observations based on source reliability, apply the trust algorithm, normalize scores, and construct a Merkle tree of the results. Operators would then sign this commitment and broadcast signatures until reaching threshold consensus.
Our smart contracts are currently just janky examples of how you could get a system like this to work, with no slashing or consensus. Eventually, they wold act as the bridge between off-chain consensus and on-chain rewards. When operators form consensus on trust scores and collect sufficient signatures, they would submit the Merkle root to an ConsensusRegistry contract. Storage providers can then claim rewards by submitting their trust score and a Merkle proof to the relevant StoragePool contract. Furthermore, operators could flag other operators for attesting to wildly out-of-band reputation scores, and slash them accordingly using the record + on-chain commitment of consensus.
Beyond the Hackathon
We’re now expanding the system to address the limitations in our initial implementation:
- Implementing full gossip-based EigenTrust
- Developing proper AVS operator rewards/slashing
- Creating a DHT for more efficient content discovery
What makes me particularly excited about Jax is how it creates a permissionless environment for storage incentive experimentation. Different applications can implement the incentive models that best fit their specific use cases without sacrificing decentralization or data availability.
The fundamental insight remains powerful: by directly measuring and rewarding the behaviors that make storage useful—actual availability and retrievability—we create a system where economic incentives naturally align with user needs. No complex cryptographic proofs or elaborate tokenomics required.
I’m looking forward to building out this vision and seeing if we can finally deliver on the long-promised potential of truly decentralized, economically sustainable file storage.